June 02, 2020
Improve Your Security Capabilities with Microsoft
Learn about Microsoft's security features and resources.

Learn how CDW and Microsoft can help you with your security challenges.
I was intrigued by the very thought there were hackers that could either A) create cracks for video games so I could play them for free, or B) create viruses that could wreak havoc on unsuspecting victims. I didn’t have Norton or McAfee or any other antivirus other than the AV that DOS 6.22 came with. This was my first experience with antivirus software.
I would run the software over and over on my machine, out of a basic fear that someone somehow got one over on me. At that time, the Michelangelo virus was in the news, and John McAfee stated that it would wipe millions of devices as it spread, though it ended up, thankfully, impacting less than 20,000 devices. Today, in my role as a Microsoft 365 pre-sales architect, I give even more thought to the security aspects of Microsoft’s environment.
The Microsoft Security Journey
From then until recently, my view of security and Microsoft have equaled somewhere in the realm of file rights and Windows firewall (which was usually disabled or turned off). In the middle of it all were episodes of exposure to Proxy 2.0 and ISA Server, and heavy doses of third-party security solutions layered onto my environments. Also, an on-again/off-again relationship with network admins setting rules that could make or break my day ― and my users’ ability to work. My background as an SCCM (System Center Configuration Manager) admin gave me many new avenues to start regulating software and threats. We were now capable of not only pushing down software and patches but regulating configuration baselines and having actionable processes to remediate out of scope configurations.
So, you may ask how Microsoft is a security company. They have not been in the past (or have they?), and they have heavily relied on third-party software vendors to handle it.
In this series of blog posts, I will explore the different points of depth that Microsoft went in their own security journey. If we have had the pleasure of talking before, some of this will sound familiar, as it explores topics I discuss daily with customers. We will go through topics like: “The holy trinity of ATPs;” “Is there security hiding in my E3 license?”; and “Making sense of the signals.” Along the way I hope to talk through scenarios where customers are using all the security suite, and how we have been able to help build that vision.
Microsoft’s Expansive Security Reach
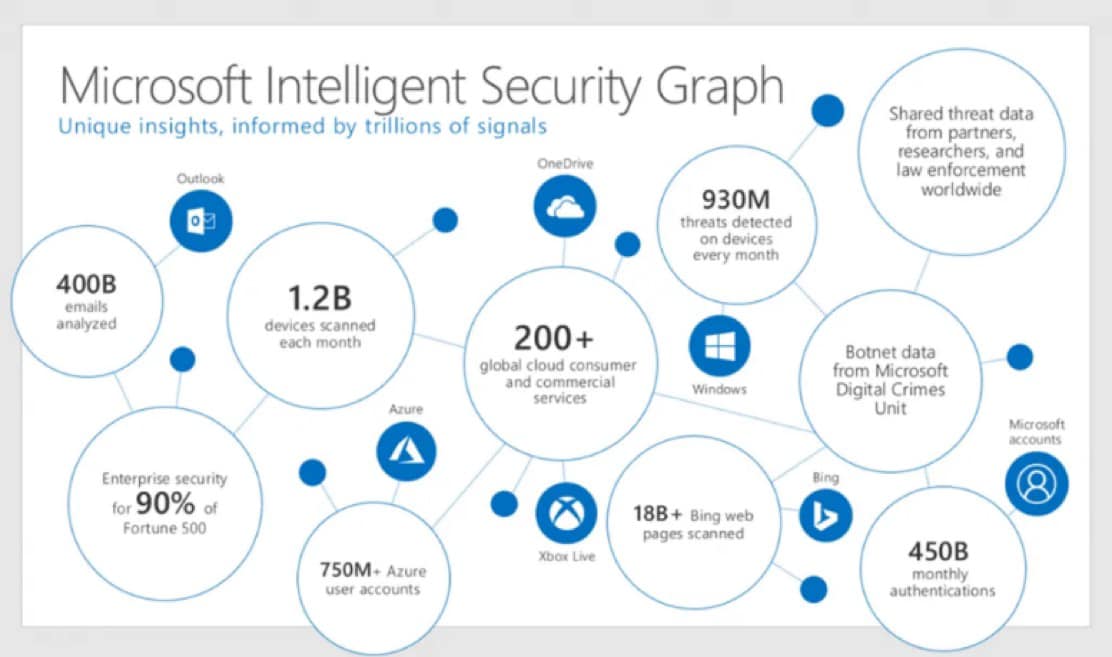
A final answer to my question: Yes, Microsoft is a security company. The company consumes over eight trillion data signals per day in its Intelligent Security Graph using AI and machine learning to determine normalized and anomalous processes. Those points of data come from every side of the exposed digital spectrum: Bing web crawling, consumer and business formats of OneDrive/Outlook, Xbox Live, and everything across the Office 365 and Azure ecosystem.
Besides this data, Microsoft takes shared threat data from partners (maybe the third-party solution you were considering). Microsoft also has its own Digital Crimes Unit, where analyzed botnet data is applied to understand threats worldwide. Using all that data, it can quickly detect, investigate and respond. (By the way, you get to reap the benefits that trickle down from all of that to your security investment and protect your digital estate.)
Microsoft currently has five security categories recognized by Gartner in the upper right quadrant: Endpoint Protection, Access Management, Cloud Access Security Broker (CASB), Information Archive, and Unified Endpoint Management (UEM). Microsoft has a unique perspective of protecting from the inside and combining data to cross reference the ebb and flow of all things, which in turn gives you the rich features to protect your own environment.
An Invitation to the Microsoft Security Ecosystem
Obviously, this is too big of a question to answer in one post. Please join me in my forthcoming posts to learn what Microsoft is doing around security. Not only does CDW know Microsoft products, but we also know consulting, design, implementation and management. We can help you get from security point A to point B, and well on your way to a return on your investment. If this has piqued your interest, consider reaching out to your account manager to learn more about our security experts and professional services.
