June 29, 2021
Building a Zero-Trust Environment with Microsoft 365
With data residing on-premises, in the cloud and beyond, IT leaders must focus on identity, security and compliance to protect it.

Today’s threat environment requires new ways of thinking about cybersecurity controls. Gone are the days when organizations could rely on physical and logical walls around their facilities and networks to control the flow of information. Today’s workforce is constantly on the move and leverages a variety of cloud services to get work done. Protecting information and resources in this environment requires shifting our trust paradigm from a focus on network location to a focus on individuals and their business needs.
The zero-trust model of cybersecurity adopts exactly this approach, building on three foundational pillars: identity, security, and governance and compliance. As organizations move toward this model, they require technology platforms that facilitate the zero-trust approach. Microsoft 365 offers a range of services that assist technologists as they start down the long road toward a zero-trust cybersecurity philosophy.
Let’s take a look at the role that Microsoft 365 plays in each one of the three zero-trust pillars.
Identity
Identity and access management programs are today’s firewalls. They serve as the first line of defense, providing strong authentication and authorization services for end users. The zero-trust model determines the identity of individual users and the roles that they play in the organization. With that information in hand, other systems and platforms can grant users the ability to access the information and resources they need to do their jobs at the appropriate times and prevent unauthorized access.
Azure Active Directory functions as an organization’s identity provider, acting as a single source of truth for identification, authentication and authorization. The centralized role of Azure AD allows administrators to quickly make enterprisewide modifications of user privileges and immediately revoke enterprisewide access when necessary.
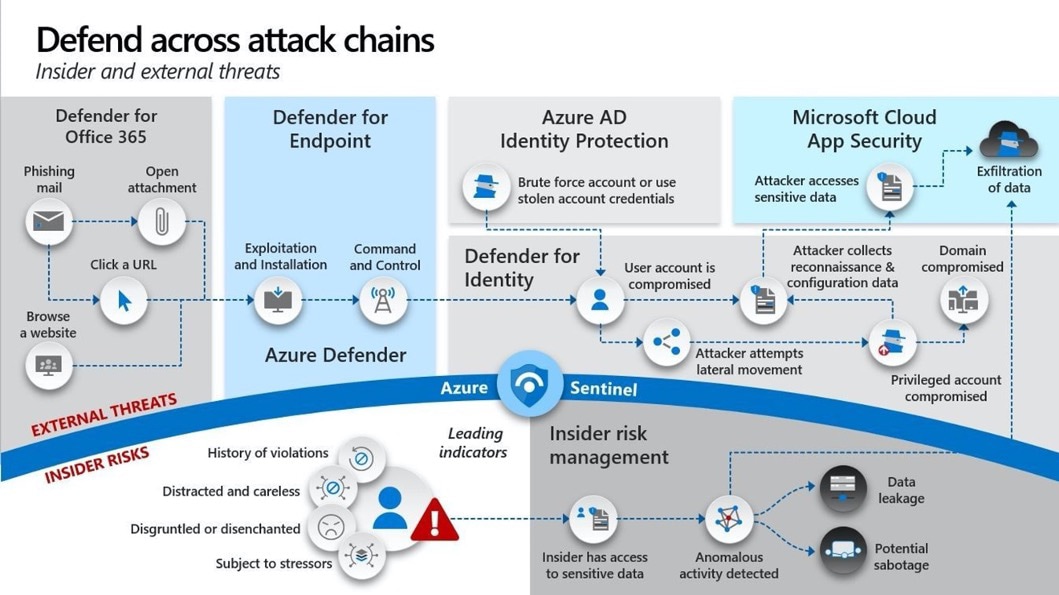
Security
Cybersecurity controls are also quickly evolving to protect against increasingly sophisticated threats. This is particularly apparent in the world of endpoint protection. Yesterday’s endpoint protection software used signature detection techniques to identify, block and remediate known threats. Today, there are simply too many new threats appearing every day for signature-based approaches to have any chance of keeping up.
Microsoft 365 provides access to endpoint detection and response capabilities that adopt a modern approach to endpoint protection. At the E3 level, Microsoft 365 provides the ability to identify and analyze potentially malicious activity, while the E5 service level allows you to automatically block and remediate security issues.
Governance and Compliance
Today’s organizations must comply with a wide variety of national, state and industry laws and regulations governing the ways that they handle sensitive information. Complying with these mandates presents a significant technological and administrative burden.
Microsoft 365 includes a number of components that assist with this work. The Microsoft Information Protection suite provides data loss prevention technology to prevent data exfiltration and offers unique “in motion” encryption capabilities that protect the security of information even after it leaves your protected environment. Microsoft Cloud App Security provides cloud access security broker capabilities that reach into cloud services to enforce your organization’s security policies wherever data resides.
Zero-trust computing promises to provide organizations with a sustainable security model that will protect their information and systems against emerging threats for years to come. Organizations that adopt Microsoft 365 services will find themselves well-positioned to deploy a zero-trust approach.

